These are commonly usable Terraform Modules for the Open Telekom Cloud based on the awesome Terraform OTC Provider.
These modules are developed by iits-consulting - your Cloud-Native Innovation Teams as a Service!
For fully integrated examples please visit the Terratest Directory You pick modules which you would like to use like this:
module "vpc" {
source = "registry.terraform.io/iits-consulting/project-factory/opentelekomcloud//modules/vpc"
version = "5.2.0"
name = "myproject-dev-vpc"
cidr_block = "192.168.0.0/16"
subnets = {
"myproject-dev-subnet" = cidrsubnet("192.168.0.0/16", 1, 0)
}
}- ACME: Create, sign and update HTTPS certificates via OTC DNS
- CCE: A module designed to support full capabilities of OTC CCE while simplifying the configuration for ease of use.
- cts: This module enables the Cloud Tracing functionality in the OTC.
- jumphost: A module designed to create SSH jumphosts via OTC ECS for private networks.
- keycloak_saml: Connects Keycloak with OTC SAML IDP
- keycloak_oidc: Connects Keycloak with OTC OIDC IDP
- loadbalancer: Module for creating an OTC ELB resource with public EIP
- obs_secrets_reader: This modules reads JSON formatted secrets from an OBS bucket.
- obs_secrets_writer: This modules creates an OBS Bucket with KMS SSE default encryption and a JSON encoded secrets file within the bucket.
- obs_restricted: This modules creates OBS bucket restricted by predefined access policy.
- private_dns: Create and manage a private DNS zone within you VPC
- public_dns: Create and manage a public DNS zone
- rds: A module designed to support full capabilities of OTC RDS while simplifying the configuration for ease of use.
- snat: Public SNAT gateway to grant internet access from a VPC without shared SNAT.
- vpn: Creates a VPN tunnel.
- waf: Create Web Application Firewall for a Domain
- evs: Create an encrypted Elastic Volume Service (EVS)
- state_bucket: Create an encrypted state bucket for Terraform
- cce_gpu_node_pool: GPU Node Pool for CCE
As a quick start we recommend using this template:
Then just adjust the set-env.sh and the showcase/dev/main.tf as you wish
There are some variables that occur on multiple modules. The ideas behind them are explained here.
| Variable | Description | Example |
|---|---|---|
context |
A human-readable name of the project | website, payments-service |
stage |
Name of the environment | dev, test, qa, prod |
The following modules are currently not working for Swiss OTC:
- public_dns: Create and manage a public DNS zone
- waf: Create Web Application Firewall for a Domain
-
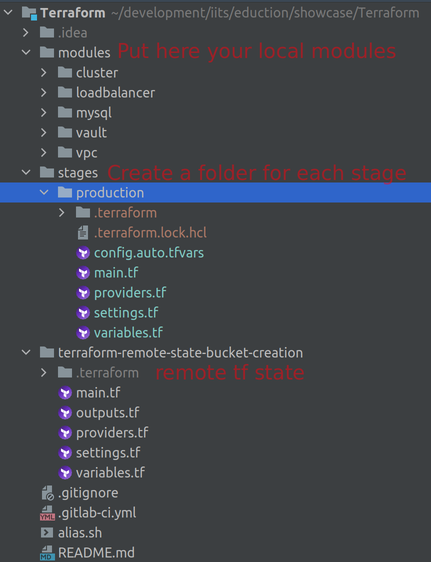
We recommend this kind of Terraform folder structure:
-
Set up a secure remote Terraform state . Copy the backend output of that module to your
settings.tffile -
Use https://github.com/iits-consulting/otc-infrastructure-charts-template if you want to use ArgoCD (GitOps)
No requirements.
No providers.
No modules.
No resources.
No inputs.
No outputs.