-
Notifications
You must be signed in to change notification settings - Fork 0
Threat Assessment
Sárváry Krisztián edited this page Oct 16, 2020
·
4 revisions
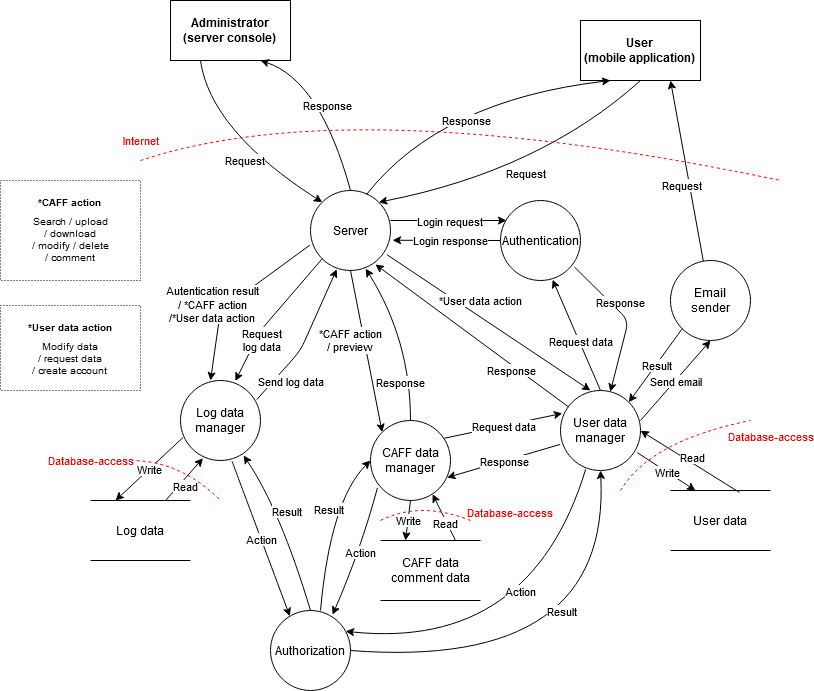
Physical assets
- server
- database
Human assets
- user
- administrator
Logical assets
- user data (email, username, password)
- CAFF and comment database
- system data (log files)
The following table contains the identified threats and possible vulnerabilities the various participants of the system could exploit.
| Threat aspects | Administrator | User | Everyone else |
|---|---|---|---|
| Spoofing | |||
| Writing comments | X | ||
| Writing comments in name of other users/administrators | X | X | X |
| Editing comments | X | ||
| Editing comments in name of other users/administrators | X | X | X |
| Uploading files | X | ||
| Uploading in name of other users/administrators | X | X | X |
| Tampering | |||
| Modification of logs | X | X | X |
| Editing the date of comment edit | X | X | X |
| Modification of the comment editors name | X | X | X |
| Editing comments of other users/administrators | X | X | |
| Downloading a CAFF file | X | ||
| Replacing CAFF file | X | X | X |
| Deleting CAFF file | X | ||
| Deleting CAFF file of other users/administrator | X | X | |
| Editing the CAFF files name | X | ||
| Editing the CAFF files name of other users/administrator | X | X | |
| Editing the CAFF files tag | X | ||
| Editing the CAFF files tag of other users/administrator | X | X | |
| Editing the username | X | ||
| Editing the username of an other user/administrator | X | X | |
| Editing the email | X | X | |
| Editing the email of an other user/administrator | X | X | X |
| Editing the password | X | X | |
| Editing the password of an other user/administrator | X | X | X |
| Repudiation | |||
| Deletion of log or log-snippet | X | X | X |
| Information disclosure | |||
| Searching of CAFF files | X | ||
| Gaining access to log files | X | X | |
| Viewing of other users/administrators data | X | X | |
| Disclosure of other users/administrators emails | X | X | X |
| Disclosure of log files | X | X | X |
| Disclosure of administrator login information | X | X | X |
| Denial of service | |||
| Making system files unusable | X | X | X |
| Making the server unreachable | X | X | X |
| Making the database unreachable | X | X | X |
| Elevation of privilege | |||
| Gaining access to log modification | X | X | X |
| Gaining access to administrator privileges | X | X | |
| Giving access to administrator privileges to untrusted party | X | X | X |
© Grotesque Gecko, 2020
- Functional Requirements and Use Cases
- Security Requirements and Objectives
- Threat Assessment
- Quality Gates
- Chosen Technologies
- Required Security Functionalities
- Structural Model of the System
- Behavioral Model of the System