-
Notifications
You must be signed in to change notification settings - Fork 0
Structural Model of the System
futobarna edited this page Oct 18, 2020
·
2 revisions
For a better understanding of the system's structure the following UML diagram has been created.
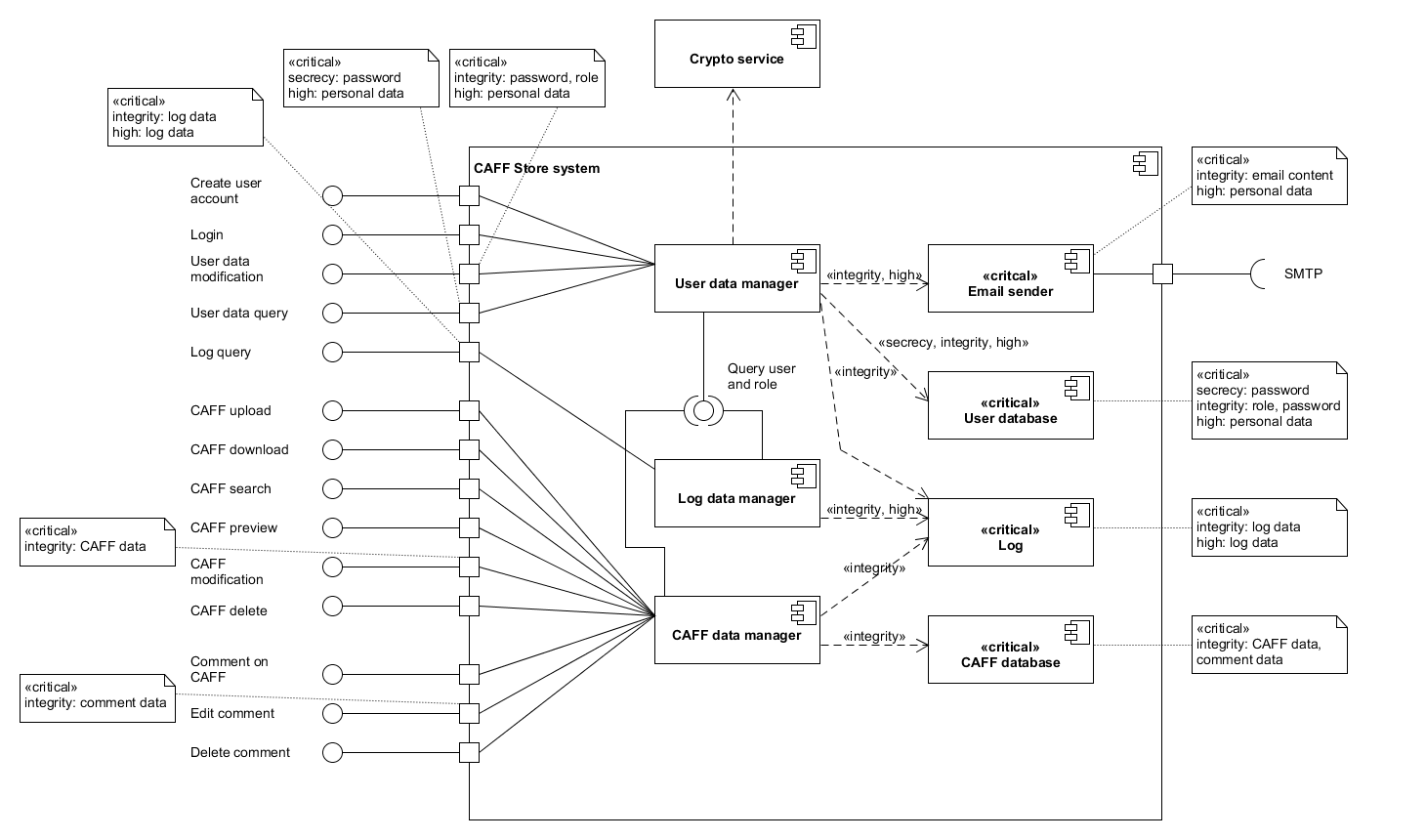
- Create user account: This interface can be used by anyone to register new accounts.
- Login: Users can use this interface to log in as an existing account.
- User data modification: Users can use this interface to change their personal data and password. Administrators can use this to change the administrator status of other users.
- User data query: This interface can be used to query the logged in user's data, or an administrator can query any user's data.
- Log query: An administrator can query the log files through this interface.
- CAFF upload: The interface used for uploading CAFF files.
- CAFF download: The interface used for downloading CAFF files.
- CAFF search: The inteface used for searching among uploaded CAFF files.
- CAFF preview: The interface used for getting CAFF previews.
- CAFF modification: The interface used for modifying CAFF files' metadata.
- Comment on CAFF: Users can use this interface to write comments on one of the uploaded CAFF files.
- Edit comment: This interface can be used to edit the logged in user's comments, or an administrator can edit any user's comment.
- Delete comment: This interface can be used to delete the logged in user's comments, or an administrator can delete any user's comment.
- SMTP: The system requires the interface of an SMTP service to send password reset e-mails.
- Query user and role: This interface provided by the User data manager is used for identifying the user and their priviliges. This is required by tasks such as querying the log files, modifying CAFF files or editing comments.
- Crypto service: The system uses an outside crypto service for cryptographically random numbers, to be used for salting passwords.
The component diagram makes use of UMLsec to signify the security requirements of certain components. This is based on the Security Requirements and Objectives, and Threat Assessment. Components that store data (databases and log) are a critical part of the system, signified by their stereotype. The Email sender is also critical, because access to it would make it possible to change any user's password without authorization. Dependencies on these components, and interfaces, that modify or read data have also been given appropriate denotations.
© Grotesque Gecko, 2020
- Functional Requirements and Use Cases
- Security Requirements and Objectives
- Threat Assessment
- Quality Gates
- Chosen Technologies
- Required Security Functionalities
- Structural Model of the System
- Behavioral Model of the System