diff --git a/network-services-pentesting/pentesting-jdwp-java-debug-wire-protocol.md b/network-services-pentesting/pentesting-jdwp-java-debug-wire-protocol.md
index 4ef04d9afad..061b133144d 100644
--- a/network-services-pentesting/pentesting-jdwp-java-debug-wire-protocol.md
+++ b/network-services-pentesting/pentesting-jdwp-java-debug-wire-protocol.md
@@ -1,23 +1,18 @@
-
+# Pentesting JDWP - Java Debug Wire Protocol
☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
-- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-
-- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-
-- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-
-- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
-
-- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
+* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
+* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
+* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
-
-# Exploiting
+## Exploiting
You can use the python exploit located in [https://github.com/IOActive/jdwp-shellifier](https://github.com/IOActive/jdwp-shellifier)
@@ -32,13 +27,13 @@ I found that the use of `--break-on 'java.lang.String.indexOf'` make the exploit
Normally this debugger is run on port 8000 and if you establish a TCP connection with the port and send "**JDWP-Handshake**", the server should respond you with the same string.\
Also, you can check this string in the network to find possible JDWP services.
-Listing **processes**, if you find the string "**jdwk**" inside a **java process**, probably it has active the **Java Debug Wired Protocol **and you may be able to move laterally or even **escalate privileges** (if executed as root).
+Listing **processes**, if you find the string "**jdwk**" inside a **java process**, probably it has active the \*\*Java Debug Wired Protocol \*\*and you may be able to move laterally or even **escalate privileges** (if executed as root).
-# More details
+## More details
**Copied from** [**https://ioactive.com/hacking-java-debug-wire-protocol-or-how/**](https://ioactive.com/hacking-java-debug-wire-protocol-or-how/)
-## **Java Debug Wire Protocol**
+### **Java Debug Wire Protocol**
**Java Platform Debug Architecture (JPDA)**: JDWP is one component of the global Java debugging system, called the Java Platform Debug Architecture (JPDA)\[2]. The following is a diagram of the overall architecture:
@@ -78,12 +73,14 @@ Welcome to Scapy (2.2.0-dev)\
An experienced security auditor may have already realised that such a simple handshake offers a way to easily uncover live JDWP services on the Internet. Just send one simple probe and check for the specific response. More interestingly, a behavior was observed on the IBM Java Development Kit when scanning with ShodanHQ\[4] with the server “talking” first with the very same banner mentioned. As a consequence, there is a totally passive way to discover an active JDWP service (this is covered later on in this article with the help of the (in)famous Shodan).\
\
-**Communication**: JDWP defines messages\[10] involved in communications between the Debugger and the Debuggee. The messages follow a simple structure, defined as follows: [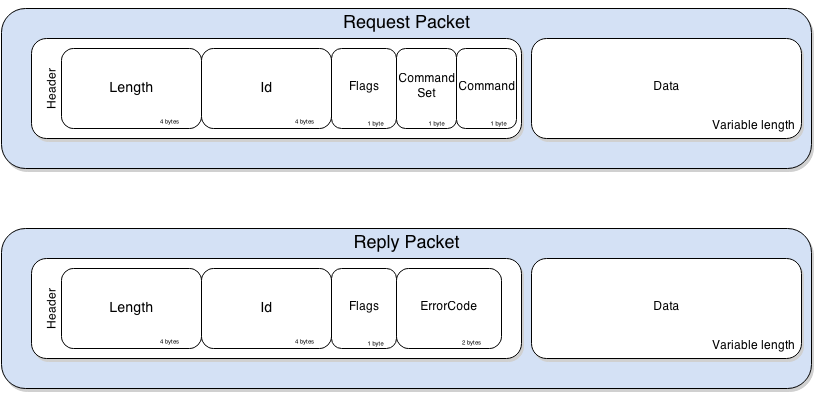](https://ioactive.com/wp-content/uploads/2014/04/createstring-1.png)
+**Communication**: JDWP defines messages\[10] involved in communications between the Debugger and the Debuggee. The messages follow a simple structure, defined as follows:
+
+
The Length and Id fields are rather self explanatory. The Flag field is only used to distinguish request packets from replies, a value of 0x80 indicating a reply packet. The CommandSet field defines the category of the Command as shown in the following table.\
\\
-| **CommandSet** | ** Command** |
+| **CommandSet** | \*\* Command\*\* |
| -------------- | ---------------------------------------------------------------------------------------------------------------- |
| 0x40 | Action to be taken by the JVM (e.g. setting a BreakPoint) |
| 0x40–0x7F | Provide event information to the debugger (e.g. the JVM has hit a BreakPoint and is waiting for further actions) |
@@ -106,13 +103,17 @@ Not only does JDWP allow you to access and invoke objects already residing in me
As we have seen, JDWP provides built-in commands to load arbitrary classes into the JVM memory and invoke already existing and/or newly loaded bytecode. The following section will cover the steps for creating exploitation code in Python, which behaves as a partial implementation of a JDI front end in order to be as reliable as possible. The main reason for this standalone exploit script is that, as a pentester, I like “head-shot” exploits. That is, when I know for sure an environment/application/protocol is vulnerable, I want to have my tool ready to exploit it right away (i.e. no PoC, which is basically the only thing that existed so far). So now that we have covered the theory, let’s get into the practical implementation. When faced with an open JDWP service, arbitrary command execution is exactly five steps away (or with this exploit, only one command line away). Here is how it would go down: 1. Fetch Java Runtime referenceThe JVM manipulates objects through their references. For this reason, our exploit must first obtain the reference to the java.lang.Runtime class. From this class, we need the reference to the getRuntime() method. This is performed by fetching all classes (AllClasses packet) and all methods in the class we are looking for (ReferenceType/Methods packet). 2. Setup breakpoint and wait for notification (asynchronous calls)This is the key to our exploit. To invoke arbitrary code, we need to be in a running thread context. To do so, a hack is to setup a breakpoint on a method which is known to be called at runtime. As seen earlier, a breakpoint in JDI is an asynchronous event whose type is set to BREAKPOINT(0x02). When hit, the JVM sends an EventData packet to our debugger, containing our breakpoint ID, and more importantly, the reference to the thread which hit it.\
\
-[](https://ioactive.com/wp-content/uploads/2014/04/event\_break-1.png)
+
+
+
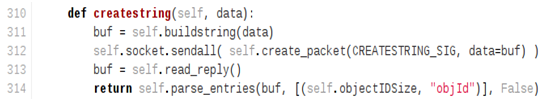
It is therefore a good idea to set it on a frequently called method, such as java.net.ServerSocket.accept(), which is very likely to be called every time the server receives a new network connection. However, one must bear in mind that it could be any method existing at runtime. 3. Allocating a Java String object in Runtime to carry out the payloadWe will execute code in the JVM runtime, so all of our manipulated data (such as string) must exist in the JVM runtime (i.e. possess an runtime reference). This is done quite easily by sending a CreateString command.
-[](https://ioactive.com/wp-content/uploads/2014/04/Untitled-1.png)
+
-4\. Get Runtime object from breakpoint contextAt this point we have almost all of the elements we need for a successful, reliable exploitation. What we are missing is a Runtime object reference. Obtaining it is easy, and we can simply execute in the JVM runtime the java.lang.Runtime.getRuntime() static method\[8] by sending a ClassType/InvokeMethod packet and providing the Runtime class and thread references. 5. Lookup and invoke exec() method in Runtime instanceThe final step is simply looking for the exec() method in the Runtime static object obtained for the previous step and invoking it (by sending a ObjectReference/InvokeMethod packet) with the String object we created in step three. [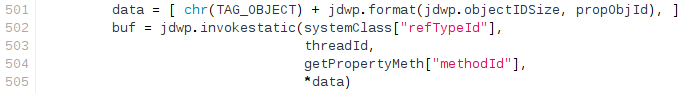](https://ioactive.com/wp-content/uploads/2014/04/exec-1.png)
+4\. Get Runtime object from breakpoint contextAt this point we have almost all of the elements we need for a successful, reliable exploitation. What we are missing is a Runtime object reference. Obtaining it is easy, and we can simply execute in the JVM runtime the java.lang.Runtime.getRuntime() static method\[8] by sending a ClassType/InvokeMethod packet and providing the Runtime class and thread references. 5. Lookup and invoke exec() method in Runtime instanceThe final step is simply looking for the exec() method in the Runtime static object obtained for the previous step and invoking it (by sending a ObjectReference/InvokeMethod packet) with the String object we created in step three.
+
+
Et voilà !! Swift and easy. As a demonstration, let’s start a Tomcat running with JPDA “debug mode” enabled:
@@ -186,7 +187,7 @@ This exploit script was successfully tested against:
As Java is platform-independent by design, commands can be executed on any operating system that Java supports. Well this is actually good news for us pentesters: **open JDWP service means reliable RCE**. So far, so good.
-## **What about real-life exploitation?**
+### **What about real-life exploitation?**
As a matter of fact, JDWP is used quite a lot in the Java application world. Pentesters might, however, not see it that often when performing remote assessments as firewalls would (and should) mostly block the port it is running on. But this does not mean that JDWP cannot be found in the wild:
@@ -209,7 +210,7 @@ These are just a few ways to discover open JDWP services on the Internet. This i
\
I would like to thank Ilja Van Sprundel and Sebastien Macke for their ideas and tests.
-## **References:**
+### **References:**
1. [https://github.com/IOActive/jdwp-shellifier](https://github.com/IOActive/jdwp-shellifier)
2. [http://docs.oracle.com/javase/7/docs/technotes/guides/jpda/architecture.html](http://docs.oracle.com/javase/7/docs/technotes/guides/jpda/architecture.html)
@@ -223,21 +224,14 @@ I would like to thank Ilja Van Sprundel and Sebastien Macke for their ideas and
10. [http://docs.oracle.com/javase/1.5.0/docs/guide/jpda/jdwp/jdwp-protocol.html](http://docs.oracle.com/javase/1.5.0/docs/guide/jpda/jdwp/jdwp-protocol.html)
11. [http://nmap.org/nsedoc/scripts/jdwp-exec.html](http://nmap.org/nsedoc/scripts/jdwp-exec.html)
-
☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
-- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-
-- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-
-- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-
-- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
-
-- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
+* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
+* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
+* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
-
-